In this article, we have shared all the basic information about Application Layer Protocols with their types, examples, uses, and functions of protocols in the application layer of the OSI Model.
What are Application Layer Protocols?
At the top of the OSI model is the Protocols application layer. It’s the layer that allows users to engage with each other. It helps the user by providing services.
An application layer is an outermost and 7th layer in the OSI Model and it is the human interaction layer, where applications can access the network services. Application layer protocols define messages exchanged by apps and actions taken.
In other words, Application layer protocols define rules when implementing specific network applications.
An application layer protocol, in particular, specifies:
- The sorts of messages, such as to request and response messages.
- The fields in the message and the syntax of the various message types
How the fields are marked out:
- The semantics of the fields, that is, the meaning of the data that the fields contain.
The field is expected to be able to hold:
- Message-sending rules that determine when and how a process sends messages
Replies to incoming messages:
- The request specifies many Internet application-layer protocols in detail.
RFCs are Requests for Comments documents that are in the public domain.
- The HTTP 1.1 standard, for example, is included in RFC 2068, which was published in 1998.
January 1997, the project was completed and made public.
- If a browser (HTTP client) developer adheres to the HTTP 1.1 RFC’s guidelines,
The browser will be able to retrieve Web pages from any Web server that has been configured to accept HTTP requests has also adhered to the HTTP 1.1 RFC’s standards.
Must Read ➜ Congestion Control
Types of Application Layer Protocols:
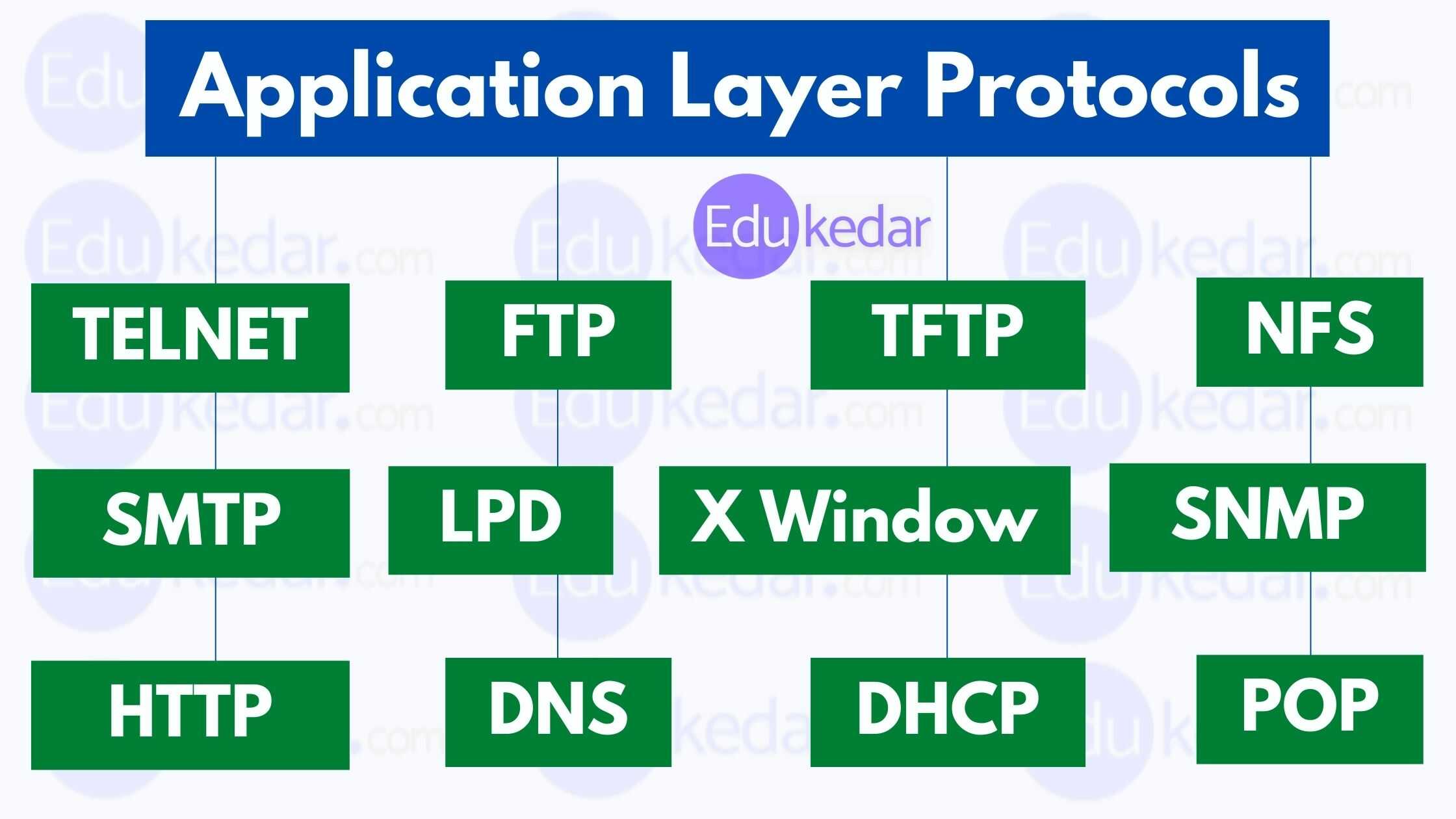
There are various types of protocols for the Application layer. Some major protocols are as follows;
- TELNET (telephone network)
- FTP (File Transfer Protocol)
- TFTP (Transfer File Transfer Protocols)
- NFS (National Football System)
- SMTP (Simple Mail Transfer Protocols)
- LPD (Leave No Trace)
- The X-window
- SNMP (Simple Network Management Protocol)
- DNS (Domain Name System)
- DHCP (Domain Name System)
1. TELNET (telephone network):
The telecommunications network is referred to as Telnet. It is beneficial to terminal emulation. It enables Telnet clients to use the Telnet server’s resources. It’s used to keep track of files on the internet. It’s used to set up devices like switches for the first time. The telnet command is a command that communicates with a remote device or system using the Telnet protocol. Telnet’s port number is 23.
The command
telnet [\\RemoteServer]
Remote server:
Specifies the name of the server you want to connect to.
2. FTP (File Transfer Protocol):
The file transfer protocol is abbreviated as FTP. It is the protocol that allows us to send and receive files. This can be done between any two machines that use it. FTP, on the other hand, is both a protocol and an application. FTP allows users to share files with others over the internet using a secure and efficient data transfer protocol. For FTP, the data port is 20 and the control port is 21.
The command
FTP machine name
3. TFTP (Transfer File Transfer Protocols):
The Trivial File Transfer Protocol (TFTP) is a stripped-down, stock version of FTP, but it’s the protocol to use if you know exactly what you’re looking for and where to look for it. It’s a simpler form of FTP that allows you to transfer files between network devices.
The command
tftp [ options... ] [host [port]] [-c command]
4. NFS (National Football System):
The acronym NFS stands for the network file system.
It allows remote computers to mount file systems across a network and interact with them as if they were locally mounted. This allows system administrators to consolidate resources on the network’s centralized servers.
The command
service NFS start
5. SMTP (Simple Mail Transfer Protocols):
Simple Mail Transfer Protocol is the abbreviation for Simple Mail Transfer Protocol. The TCP/IP protocol includes it. SMTP transmits your email on and across networks via a procedure known as “store and forward.” It collaborates with the Mail Transfer Agent (MTA) to deliver your message to the correct computer and email mailbox. The SMTP port number is 25.
The commands
MAIL FROM:<[email protected]?
6. LPD (Leave No Trace):
- The acronym LPD stands for Line Printer Daemon.
- It’s made for shared printers.
- It’s the section that takes the request and processes it. A server or agent is referred to as a “daemon.”
The command
lpd [ -d ] [ -l ] [ -D DebugOutputFile]
7. The X-window
It specifies a protocol for creating client/server applications with a graphical user interface. The concept is to execute an application called a client on a single machine. It’s mostly utilized in interconnected mainframe networks.
The command
Run xdm in run level 5
8. SNMP (Simple Network Management Protocol):
Simple Network Management Protocol is the abbreviation for Simple Network Management Protocol. It collects data by polling the devices on the network.
The network at specified or random intervals from a control station, needing
They are required to reveal specific details. It’s a mechanism for servers to share information about their present status, as well as a mechanism for administrators to change pre-defined settings. The SNMP port numbers are 161 (TCP) and 162 (UDP) (UDP).
The command
snmpget -mALL -v1 -cpublic snmp_agent_Ip_address sysName.0
9. DNS (Domain Name System):
Every time you use a domain name, a DNS provider must translate the name into an IP address. The domain name www.abc.com, for example, could be translated to 198.105.232.4.
The DNS port number is 53.
The command
ipconfig /flushdns
10. DHCP (Domain Name System):
Dynamic Host Configuration Protocol is an acronym for Dynamic Host Configuration Protocol (DHCP).
It assigns IP addresses to servers.
When a computer registers for an IP address with a DHCP server, the DHCP server can offer a lot of information to the host. The DHCP port numbers are 67 and 68.
The command
clear ip dhcp binding {address | * }
Must Read ➜ Types of Routing Protocols
Functions of the Application Layer Protocols
During a communication session, both the source and destination devices use application layer protocols. The application layer protocols deployed on the source and destination hosts must match for the communications to be successful.
Protocols carry out the following functions:
- Create a set of rules for transferring data between applications and services that have been loaded. on the devices that are taking part
- Specify the structure of the data contained in the messages, as well as the sorts of messages that are sent.
- Between the source and the destination, These messages could be service requests, for example.
- Acknowledgments, data messages, status messages, or error messages are all examples of messages.
- Define message dialogues to ensure that a message is received by the intended recipient.
- When data is transferred, ensure that the appropriate services are activated.
- Across data networks, many different types of applications communicate. As a result, the application
- To deliver the appropriate breadth of communication experiences, layer services must implement several protocols. Each protocol serves a certain purpose and has the features listed below.
- Required to achieve that goal Each layer’s protocol details must be followed in order for this to work.
- Ensure the functions on one layer communicate with the services on the lower tier properly.
- In the course of a single communication, applications and services can use different protocols. One protocol may specify how to create a network connection, while another may explain how to maintain the connection.