User Datagram Protocol, in short UDP, is one of the core members of the Internet protocol suite In computer networking.
Computer applications can send messages with the help of UDP. It is referred to as datagrams, to other hosts on an Internet Protocol network.
In this article, we have shared all the basic information, functions, and applications of the User Datagram Protocol. We have also answered questions like how important is UDP in mitigating DDoS attacks?
So let’s start our topic with the introduction to User Datagram Protocol.
What is User Datagram Protocol?
User Datagram Protocol (UDP) is a component of the Internet Protocol suite, also known as the UDP/IP suite. It is an unreliable and connectionless protocol, unlike TCP. As a result, there is no need to establish a connection before transferring data.
Despite the fact that Transmission Control Protocol (TCP) is the most widely used transport layer protocol for most Internet services, it provides guaranteed delivery, reliability, and much more, all of these benefits come at a cost in terms of overhead and delay.
UDP is used in this case. UDP(User Datagram Protocol) is required for real-time applications such as computer gaming, phone or video communication, and live the conference.
Because great throughput is required, UDP allows packets to be dropped rather than processed. Because UDP does not do error checking, it saves bandwidth.
In terms of latency and bandwidth, the User Datagram Protocol (UDP) is more efficient.
UDP Header (Uniform Datagram Protocol)
The UDP header is an 8-byte fixed and simple header, whereas the TCP header can range from 20 to 60 bytes. The first 8 bytes contain the necessary header information, while the remainder is data.
Because each UDP port number field is 16 bits long, the range for port numbers is 0 to 65535; port number 0 is reserved.
Port numbers are used to differentiate between different user requests or processes.
Source Port: Source Port is a two-byte parameter that identifies the source’s port number.
Destination Port: This is a two-byte field that identifies the destined packet’s port.
The length of UDP, including the header and data, is measured in bytes. It’s a field with 16 bits.
Checksum: The checksum is a two-byte field. It’s the 16-bit one’s complement sum of the UDP header, pseudo-IP header information, and data, padded with zero octets at the end (if necessary) to make a multiple of two octets.
Notes – Unlike TCP, UDP does not require checksum calculation. UDP does not provide error control or flow control. As a result, UDP relies on IP and ICMP to report errors.
Must Read ➜ Congestion Control
User Datagram Protocol (UDP) Applications include:
- When the size of the data is small, there is less concern about flow and error control, hence it is used for simple request-response communication.
- Because UDP provides packet switching, it is a good protocol for multicasting.
- Some routing update protocols, such as RIP, employ UDP (Routing Information Protocol).
- Typically employed in real-time applications where unequal delays between sections of a received message cannot be tolerated.
Use of UDP (User Datagram Protocol)
UDP is used as a transport layer protocol in the following implementations:
- NTP is a non-profit organization dedicated to (Network Time Protocol)
- DNS (Domain Name System) (Domain Name Service)
- DHCP, BOOTP
- NNP (Network News Protocol)
- Protocol for the Quote of the Day
- TFTP, RTSP, and RIP are examples of protocols.
- Some tasks can be performed by the application layer via UDP.
- Trace Your Steps
- Make a note of your route.
- Date and time stamp
- UDP receives datagrams from the Network Layer, attaches their headers, and sends them to the user. As a result, it operates quickly.
- If you delete the checksum field from UDP, it becomes a null protocol.
- Reduce the number of computing resources required.
- When transferring using Multicast or Broadcast.
- Real-time packet transmission, primarily in multimedia applications.
UDP Process: How does User Datagram Protocol work?
UDP is a defined technique for sending data between two computers on a network, just like all other networking protocols.
UDP performs this task in a straightforward manner as compared to other protocols:
it delivers packets (units of data transmission) immediately to a destination computer without first establishing a connection, identifying the order of such packets, or verifying that they arrived as intended. (Datagrams are the term for UDP packets.)
TCP, another common transport protocol, is quicker but less dependable than UDP. The two computers in a TCP conversation start by establishing a connection using an automated process known as a “handshake.”
Only once this handshake is complete will one computer begin sending data packets to the other.
This is not the case with UDP communications. Rather, one computer can just start transferring data to the other:
Must Read ➜ Types of Routing Protocols
TCP vs UDP: Communication Protocols
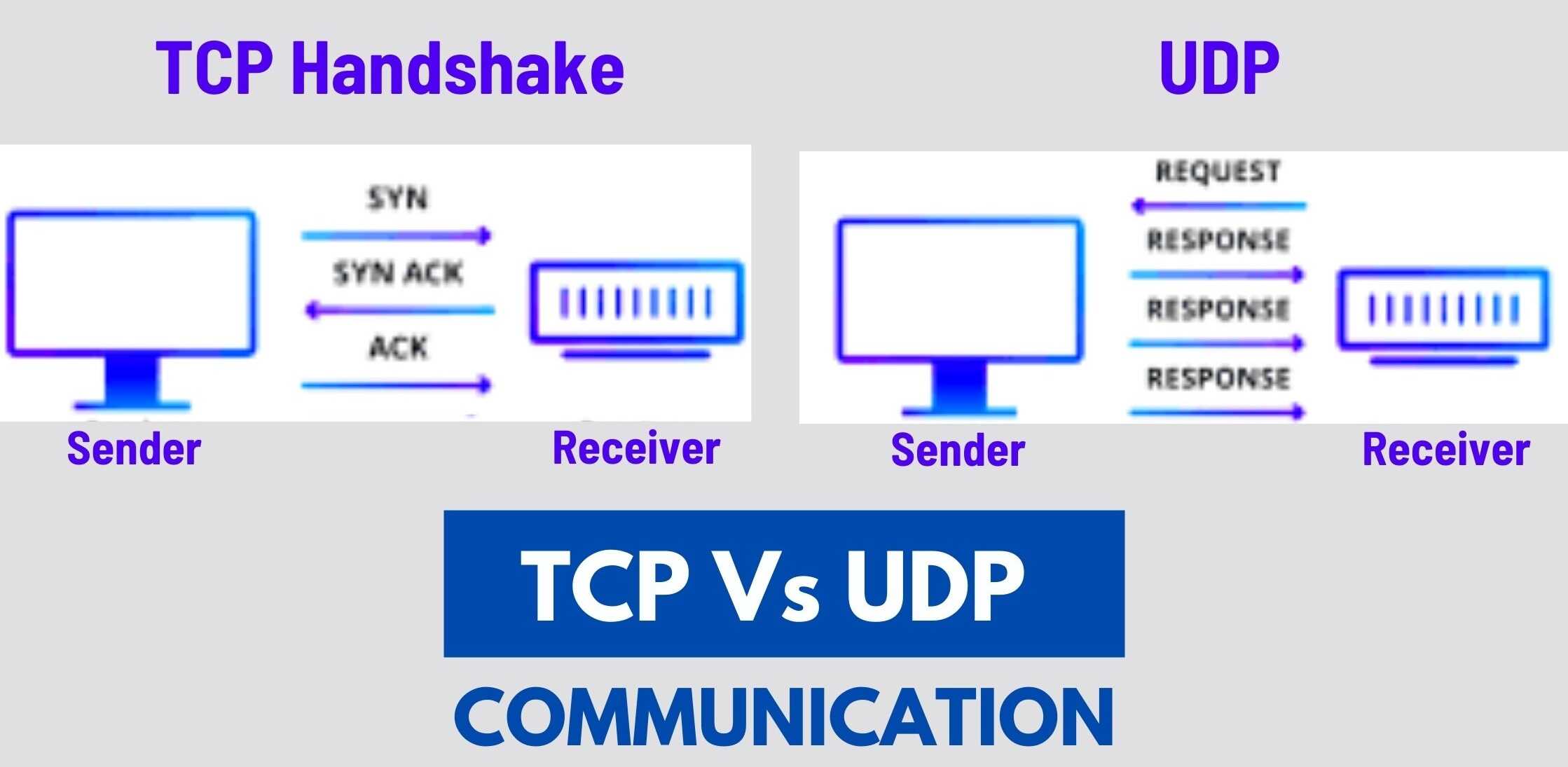
TCP communications also specify the order in which data packets should be received and check that they arrive in the correct sequence. TCP specifies that if a packet does not arrive for example, due to congestion in intermediary networks it is resent.
None of this functionality is included in UDP communications.
These distinctions provide certain advantages. User Datagram Protocol can send data quicker than TCP since it does not require a “handshake” or any checks to ensure that data arrives correctly.
However, there are costs associated with this speed. A User Datagram Protocol datagram will not be resent if it is lost in transit.
As a result, User Datagram Protocol applications must be tolerant of errors, loss, and duplication.
(Technically, packet loss is more a result of how the Internet is structured than a problem with UDP. Because doing so would demand an unrealistic amount of additional memory, most network routers do not conduct packet ordering and arrival confirmation by default. When an application requires it, TCP is a technique to bridge the gap.)
Must Read ➜ Recursion Function in Python
What Types Of Services Use UDP?
User Datagram Protocol is widely employed in time-sensitive communications where losing packets on occasion is preferable to waiting.
This protocol is used to send voice and video traffic because they are both time-sensitive and engineered to handle some loss.
For example, User Datagram Protocol is utilized by VOIP (voice over IP), which is utilized by many internet-based telephone services. This is due to the fact that a staticky phone conversation is better than one that is crystal clear but is much delayed.
As a result, User Datagram Protocol is an excellent choice for online gaming. DNS servers, likewise, employ UDP since they must be quick and efficient.
Role of UDP in preventing DDoS attacks
In most use scenarios, UDP’s ‘risks,’ such as packet loss, aren’t a severe issue. UDP, on the other hand, can be used for nefarious reasons.
Because User Datagram Protocol does not require a handshake, attackers can ‘flood’ a targeted server with User Datagram Protocol traffic without first obtaining authorization from that server to communicate.
A typical User Datagram Protocol flood attack sends a huge number of User Datagram Protocol datagrams to the target computer’s random ports.
This forces the target to respond with an equivalent amount of ICMP packets, indicating that those ports are no longer reachable.
The computational resources necessary to reply to each false datagram can exhaust the target, causing legitimate traffic to be denied service.
Organizations can defend themselves from User Datagram Protocol flood attacks in a number of ways. One alternative is to limit the rate at which ICMP packets respond, albeit this method can also filter out genuine messages.
Another option is to accept and reply to User Datagram Protocol traffic over a network of multiple scattered data centers, which prevents a single origin server from becoming overburdened with false requests.





